King Sanders
👋🏽 King Sanders – Cybersecurity Portfolio
🌐 Portfolio Website: https://cyberbeastking.github.io/
| **Entry-Level SOC Analyst | Cybersecurity Professional in Training** |
Passionate about protecting organizations through threat detection, log analysis, and incident response. Currently completing the Google Cybersecurity Certificate while building a home SOC lab with Linux, Splunk, and Security Onion. Hands-on practice includes analyzing suspicious logins, documenting incidents, and performing basic vulnerability assessments.
I bring consistency, energy, and a growth mindset — ready to contribute to a SOC team on Day One.
🧠 Skills & Tools
- Log analysis & incident documentation
- SIEM workflows (Splunk, Security Onion – home lab practice)
- Linux command-line for log navigation & user management
- SQL queries for failed login investigations & device reports
- Network monitoring & packet analysis (Wireshark, tcpdump)
- Cybersecurity tools: nmap, whois, nslookup
- Constant learner (daily labs, podcasts, certifications)
🔐 Certifications
- Foundations of Cybersecurity
- Tools of the Trade: Linux and SQL
- Connect and Protect: Networks and Network Security
- Play It Safe: Manage Security Risks
- Assets, Threats, and Vulnerabilities
- Sound the Alarm: Detection and Response
📊 Projects
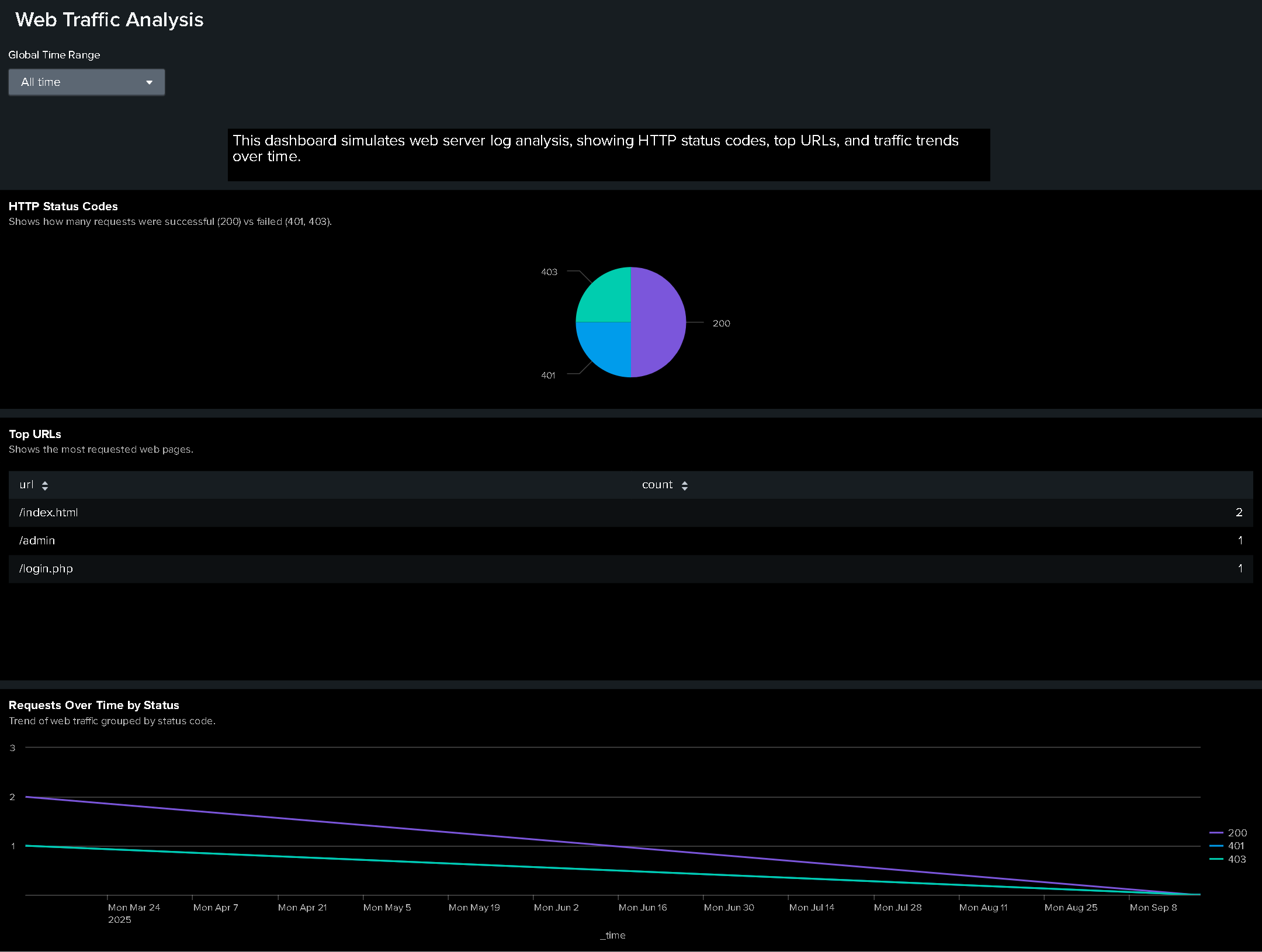
Project 1 — Web Traffic Analysis with Splunk
A security-focused dashboard built from custom web logs to show how I ingest data, write SPL, and design visualizations.
Data
- Index:
project1 - Sourcetype:
web:logs - File:
web_logs.log(sample HTTP access logs)
Screenshot
See SPL Queries - Click to Expand
1) HTTP Status Codes
index=project1 sourcetype=web:logs
| stats count by status
| sort - count
2) Requests by URL
index=project1 sourcetype=web:logs
| stats count by url
| sort - count
3) Requests Over Time by Status
index=project1 sourcetype=web:logs
| timechart span=10m count by status
4) Top Source IPs
index=project1 sourcetype=web:logs
| stats count by src_ip
| sort - count
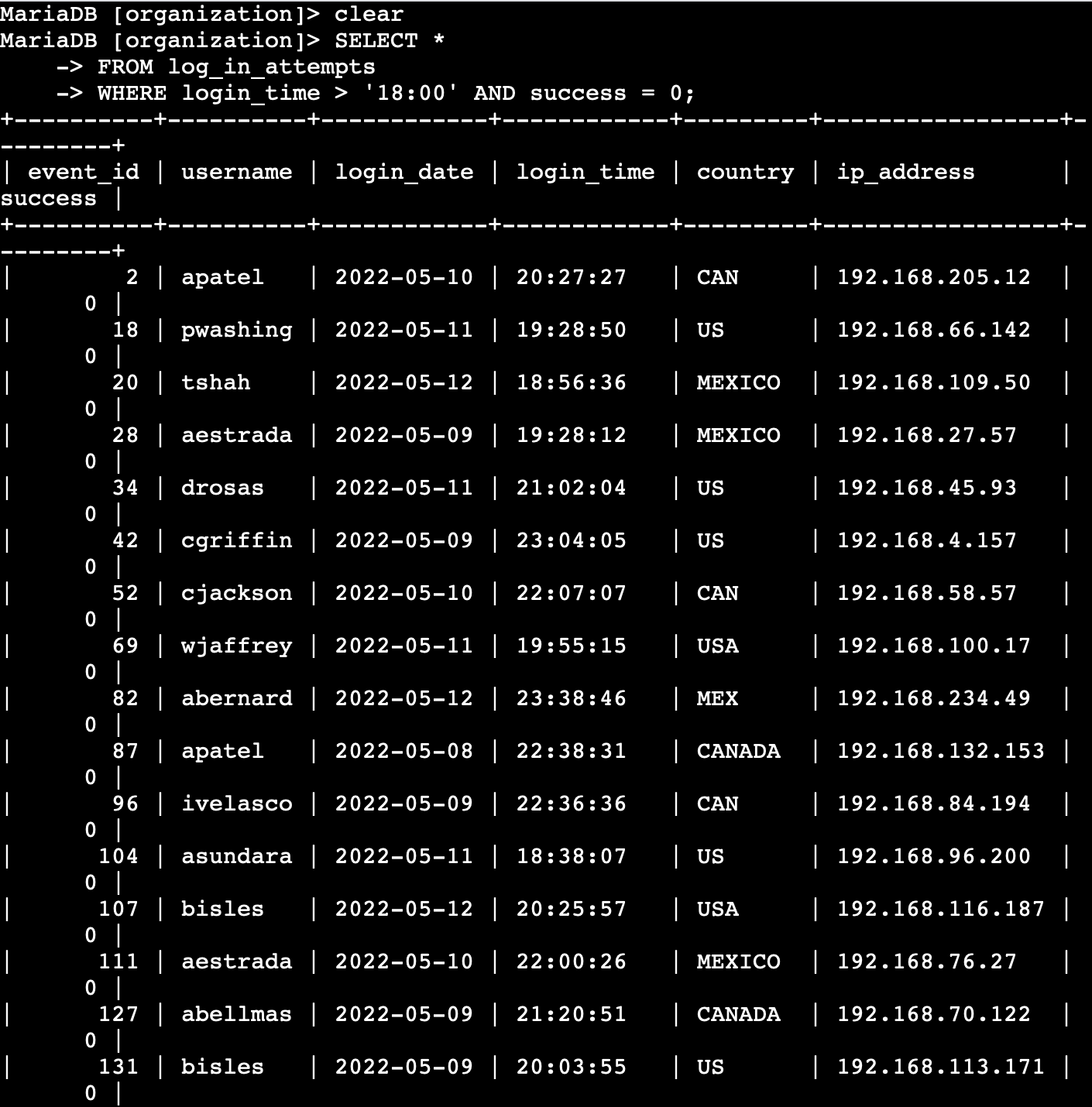
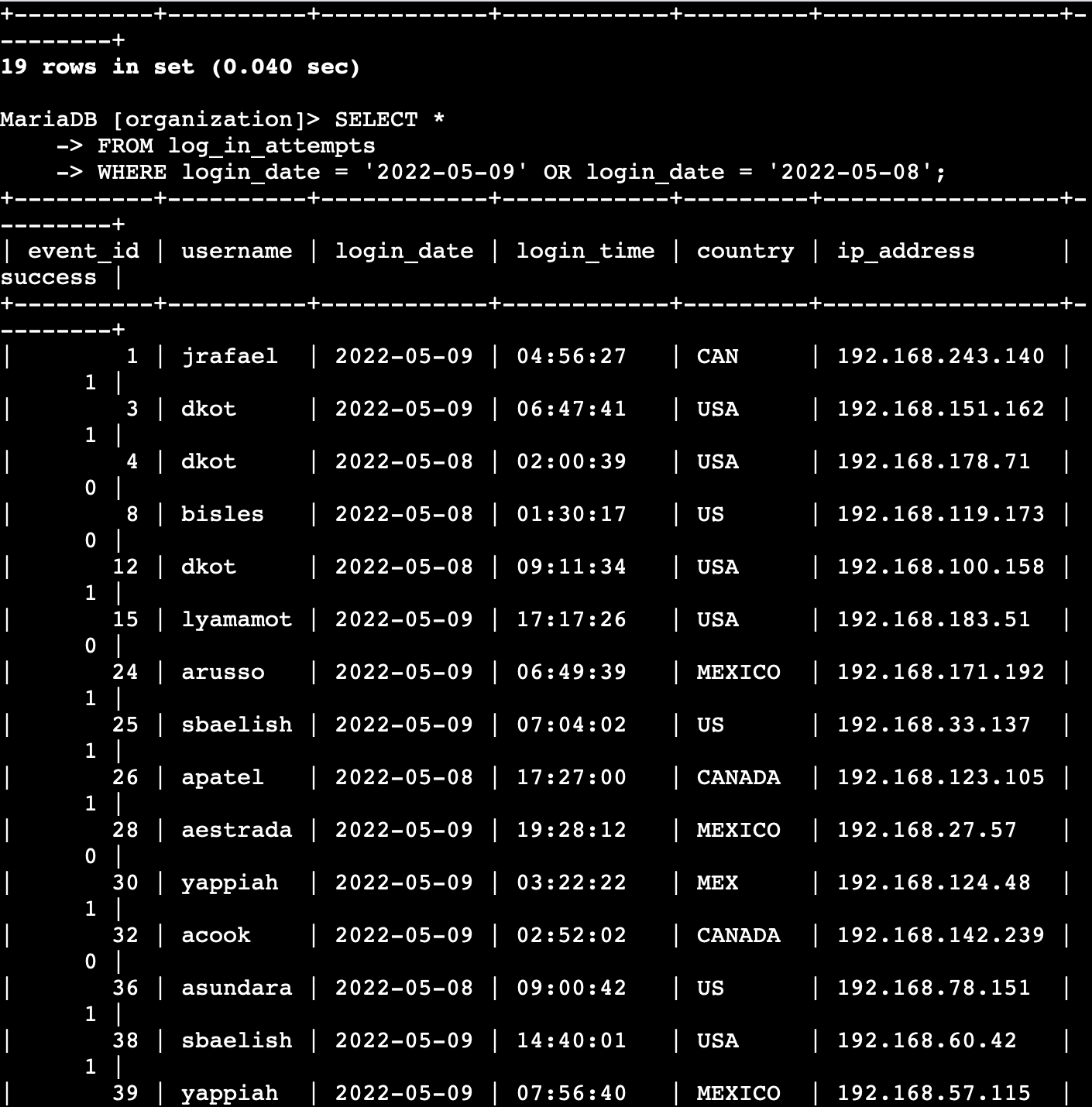
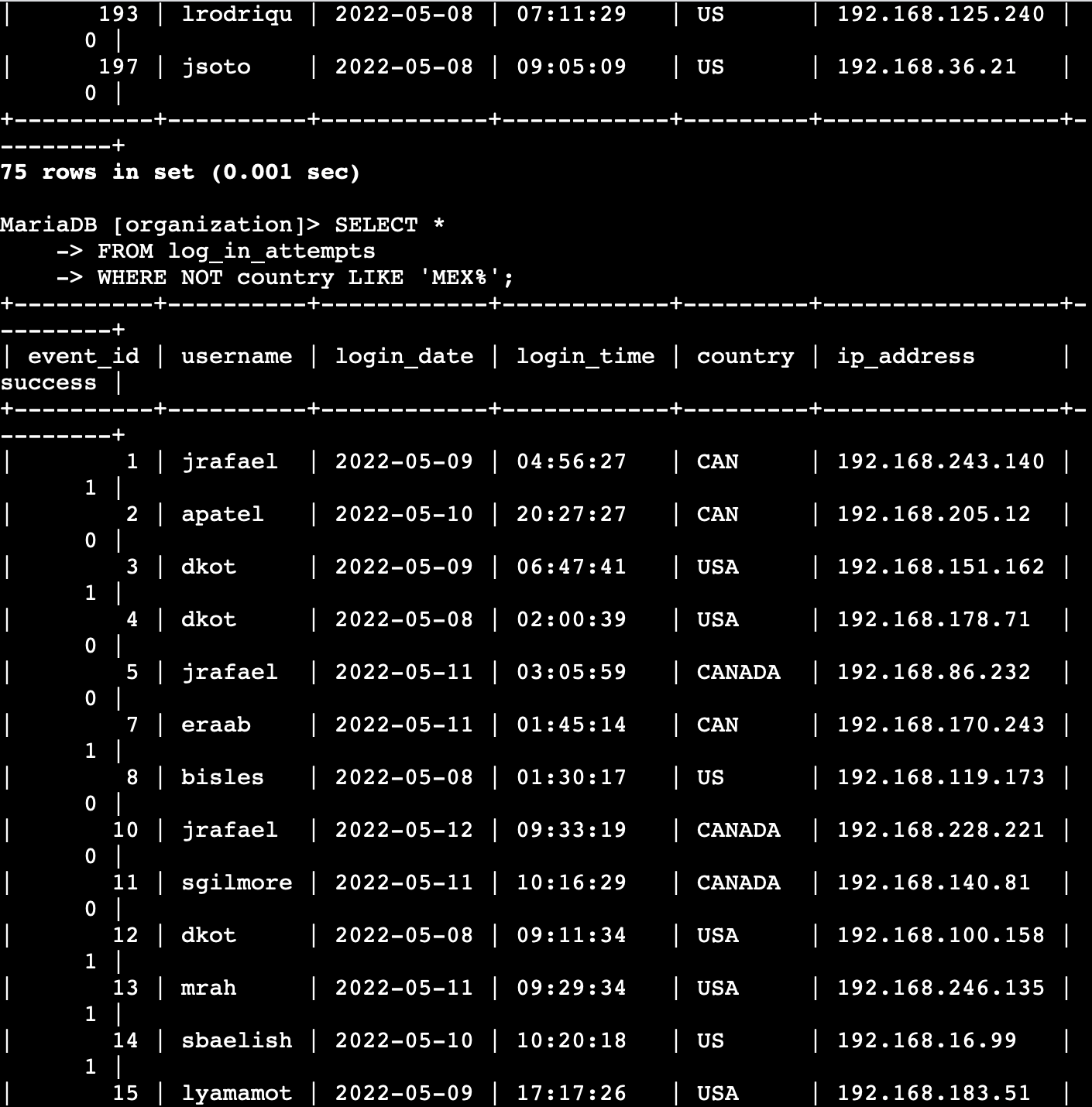
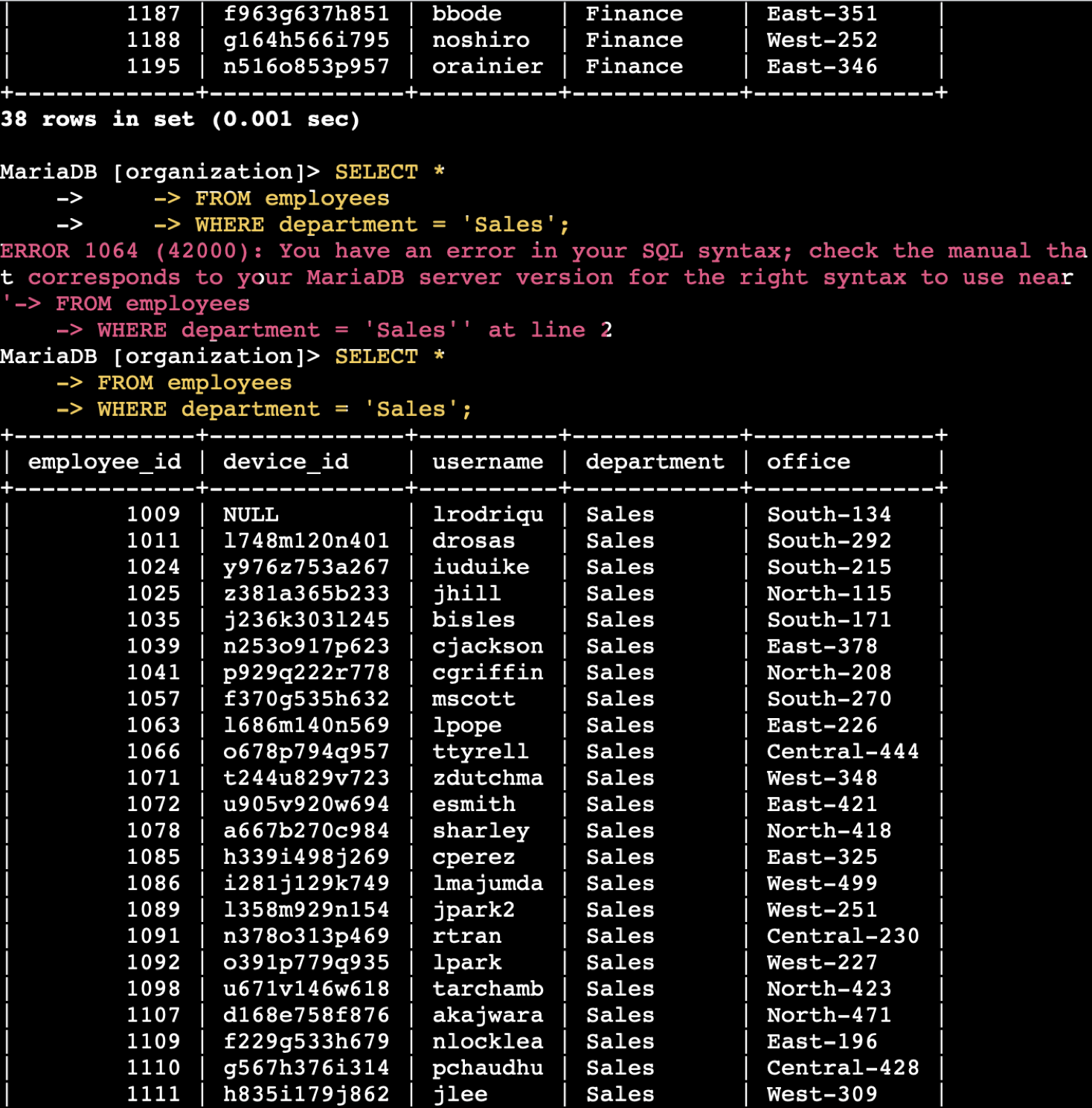
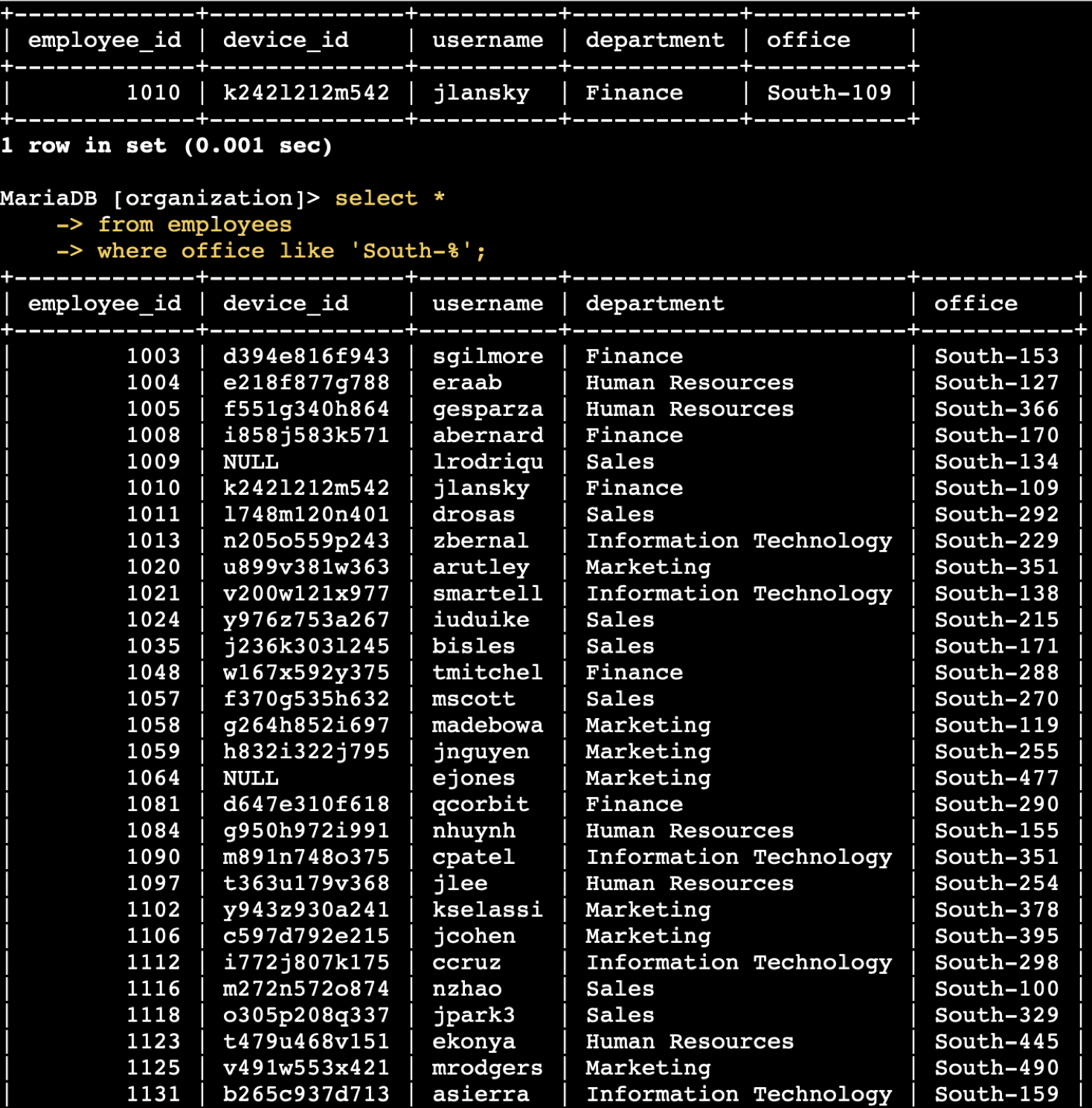
SQL Log Analysis – Suspicious Logins
This project simulates a brute-force login investigation using SQL queries on employee login data. The goal was to detect failed login attempts, external access, and suspicious login patterns.
Dataset
A synthetic employee_logins table with:
username – Employee username
login_time – Timestamp of login
ip_address – Source IP
status – SUCCESS / FAILED
Screenshots - Click to Expand
See SQL Queries - Click to Expand
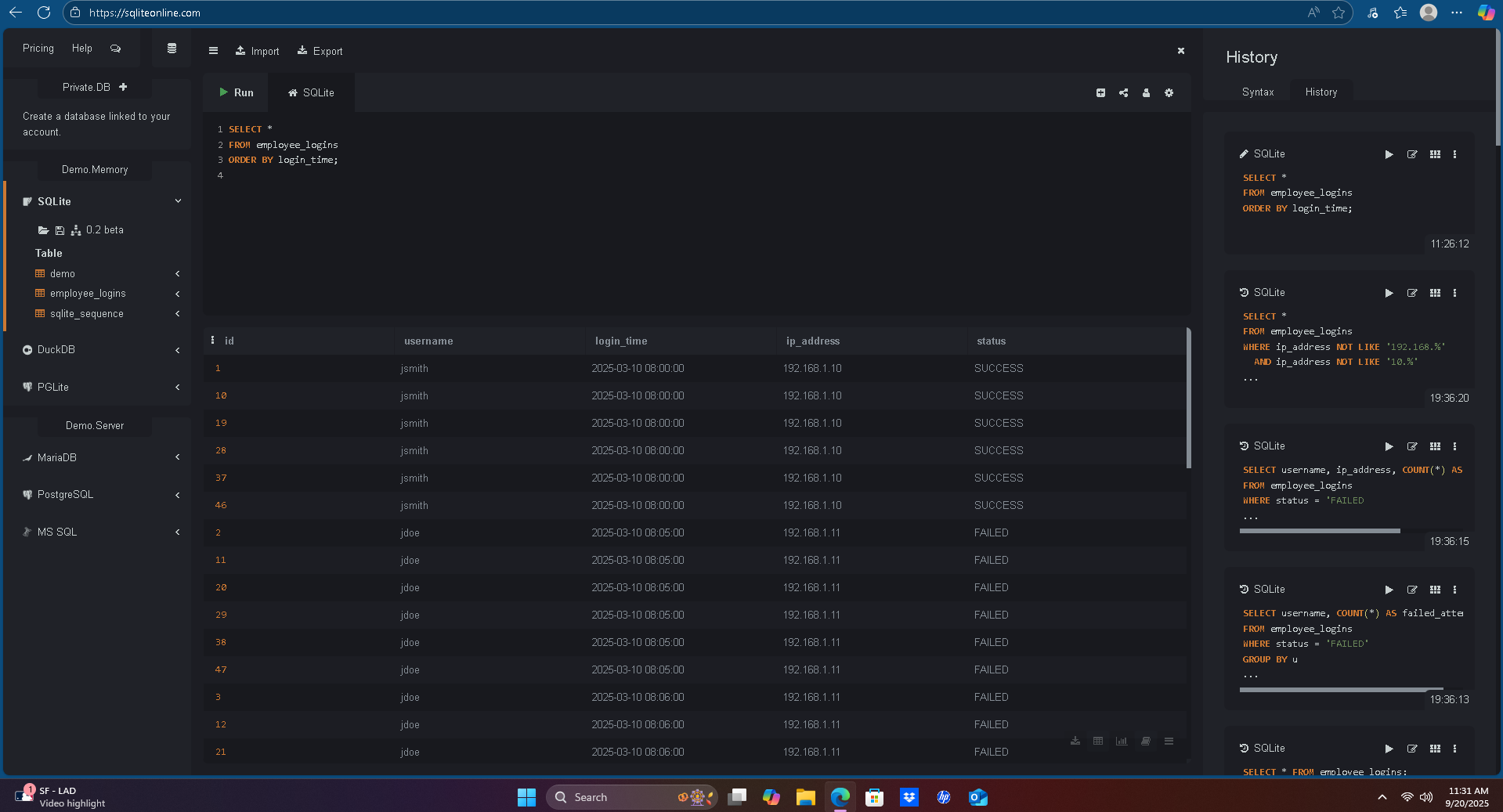
#### 1) All Login Records
SELECT *
FROM employee_logins
ORDER BY login_time;
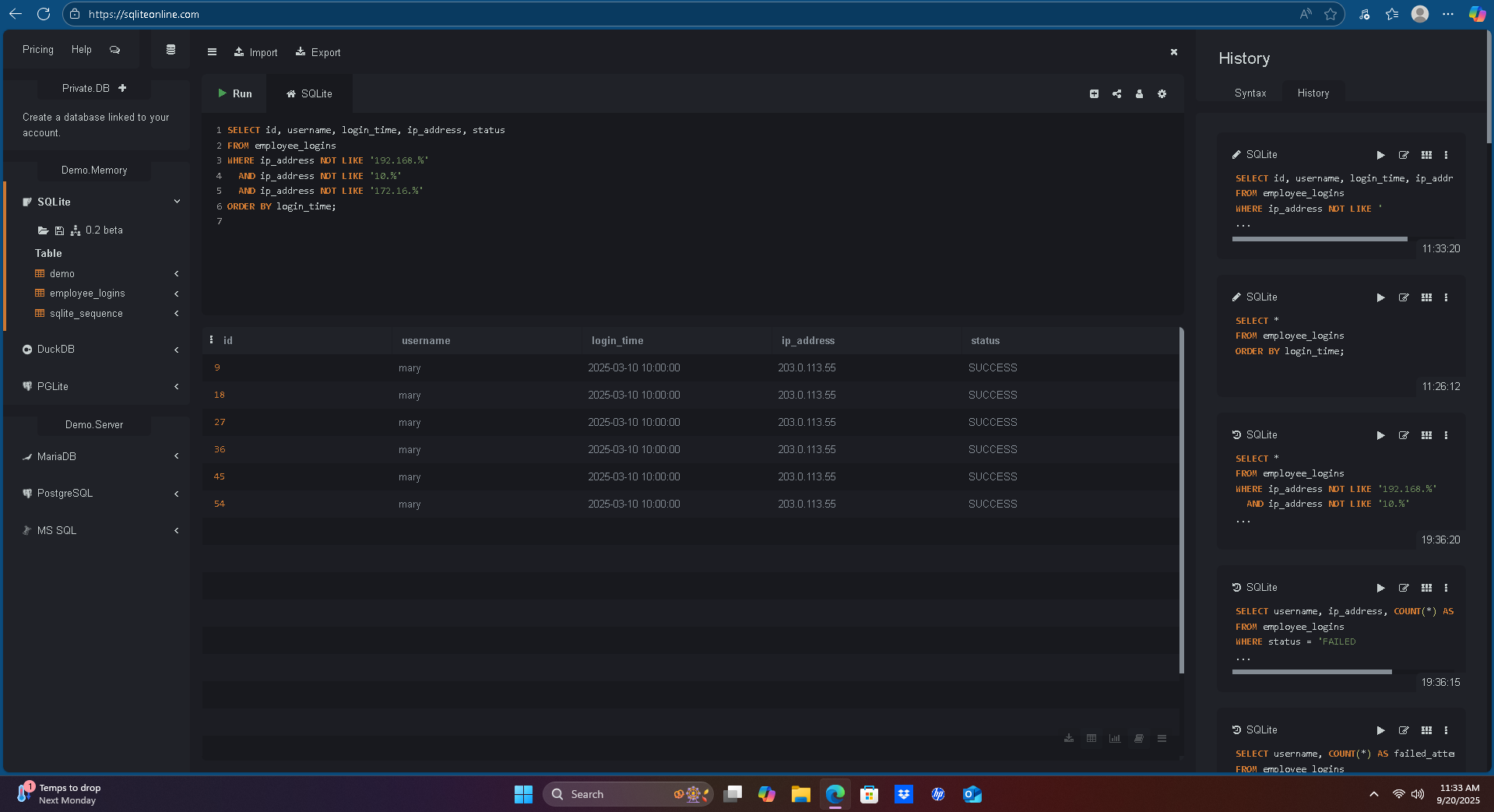
2)External Logins (Outside Internal IP Range)
SELECT id, username, login_time, ip_address, status
FROM employee_logins
WHERE ip_address NOT LIKE '192.168.%'
AND ip_address NOT LIKE '10.%'
AND ip_address NOT LIKE '172.16.%'
ORDER BY login_time;
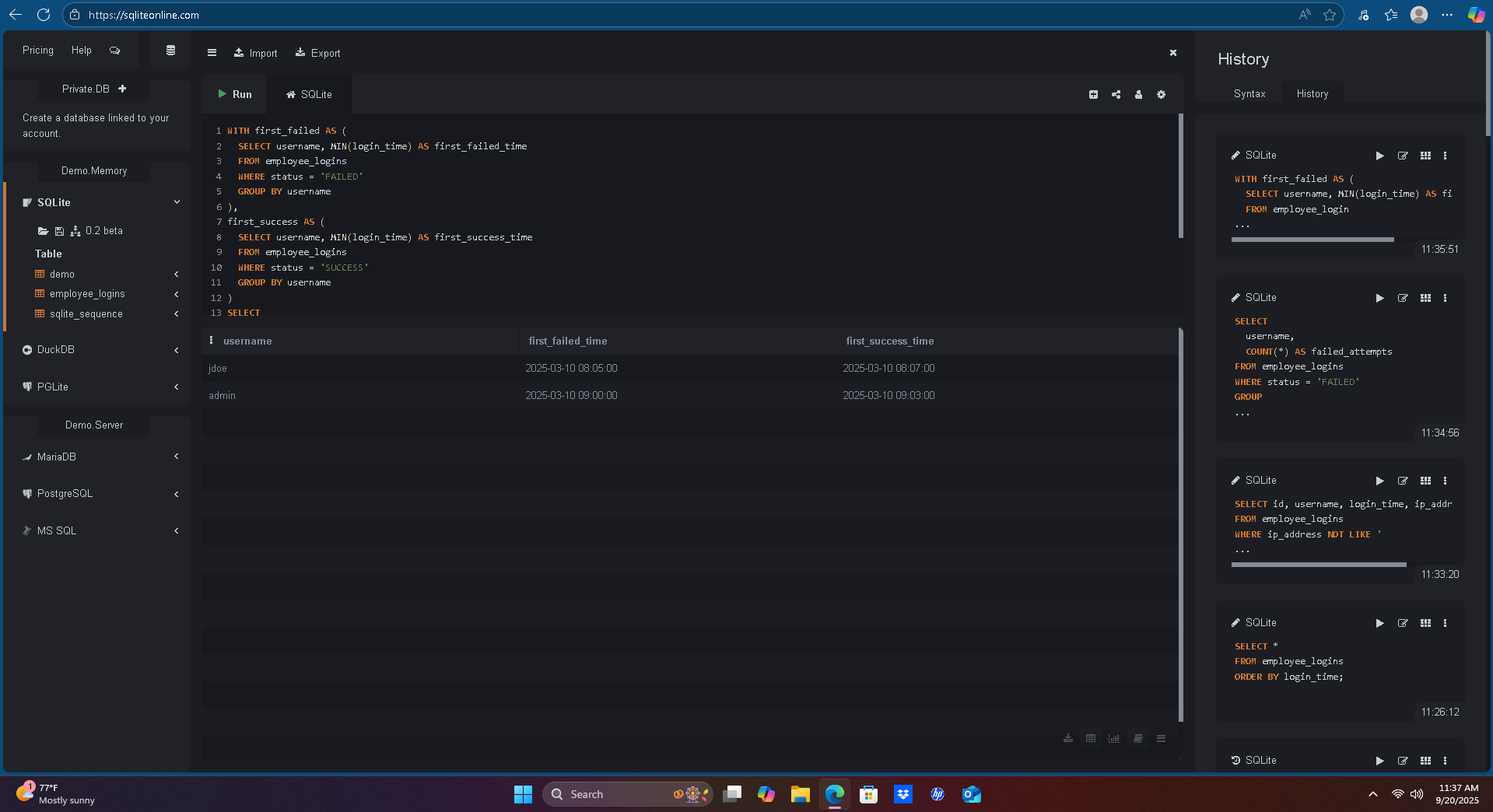
3)First Failed → First Success (Suspicious Sequence)
WITH first_failed AS (
SELECT username, MIN(login_time) AS first_failed_time
FROM employee_logins
WHERE status = 'FAILED'
GROUP BY username
),
first_success AS (
SELECT username, MIN(login_time) AS first_success_time
FROM employee_logins
WHERE status = 'SUCCESS'
GROUP BY username
)
SELECT f.username, f.first_failed_time, s.first_success_time
FROM first_failed f
JOIN first_success s ON f.username = s.username;
4) Failed Attempts per IP
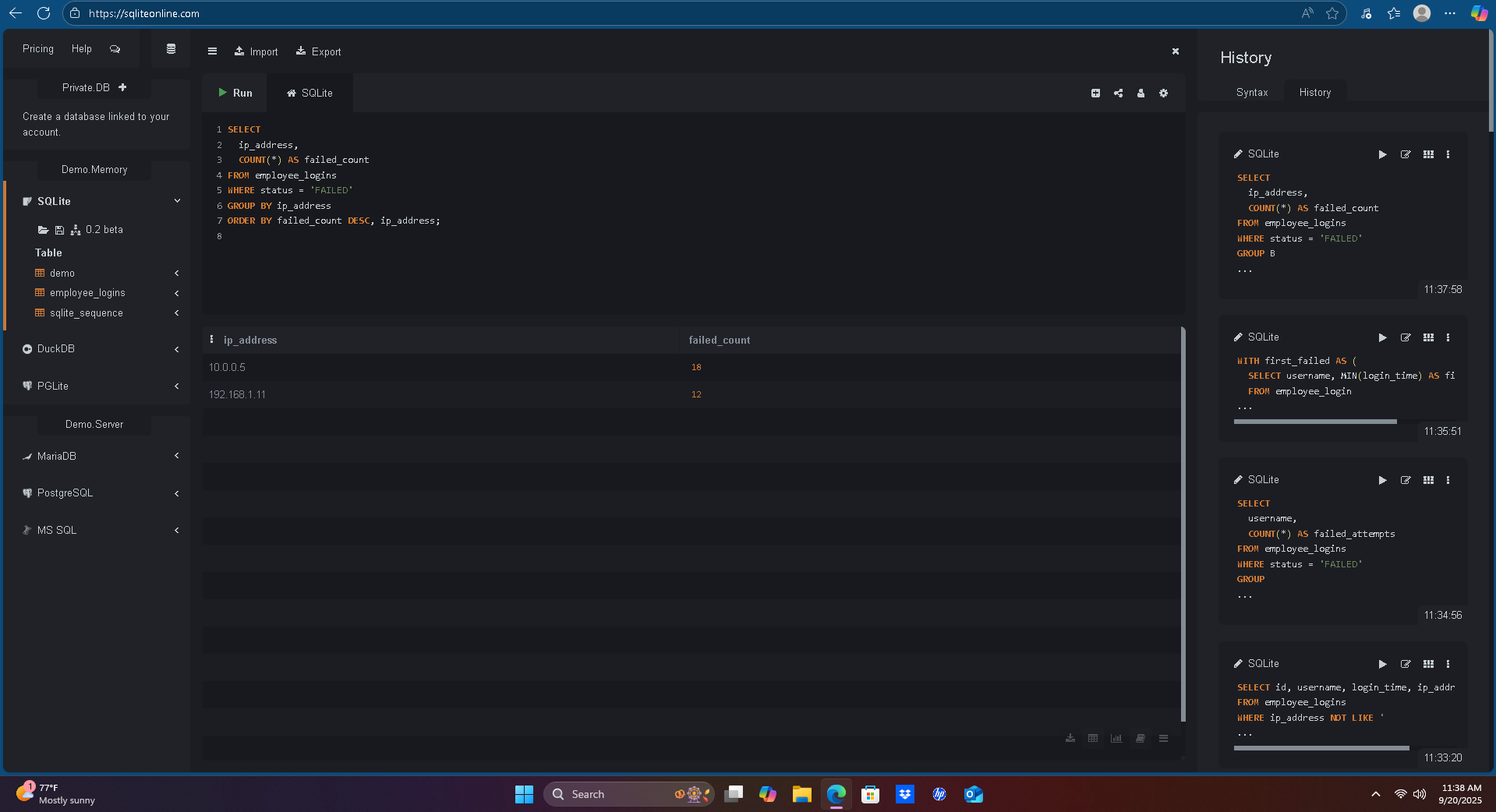
SELECT ip_address, COUNT(*) AS failed_count
FROM employee_logins
WHERE status = 'FAILED'
GROUP BY ip_address
ORDER BY failed_count DESC, ip_address;
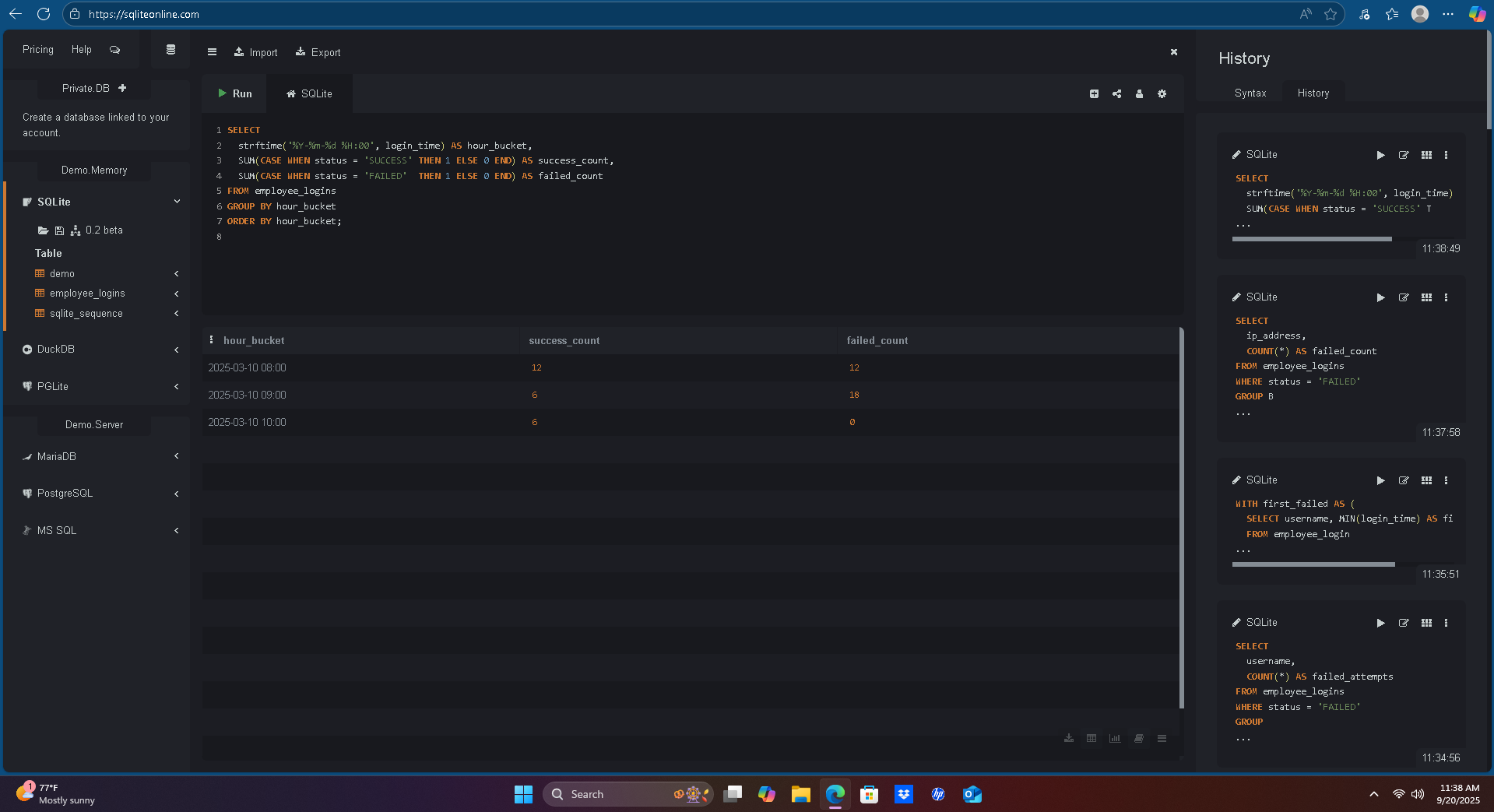
5) Logins Over Time (by Hour)
SELECT strftime('%Y-%m-%d %H:00', login_time) AS hour_bucket,
SUM(CASE WHEN status = 'SUCCESS' THEN 1 ELSE 0 END) AS success_count,
SUM(CASE WHEN status = 'FAILED' THEN 1 ELSE 0 END) AS failed_count
FROM employee_logins
GROUP BY hour_bucket
ORDER BY hour_bucket;
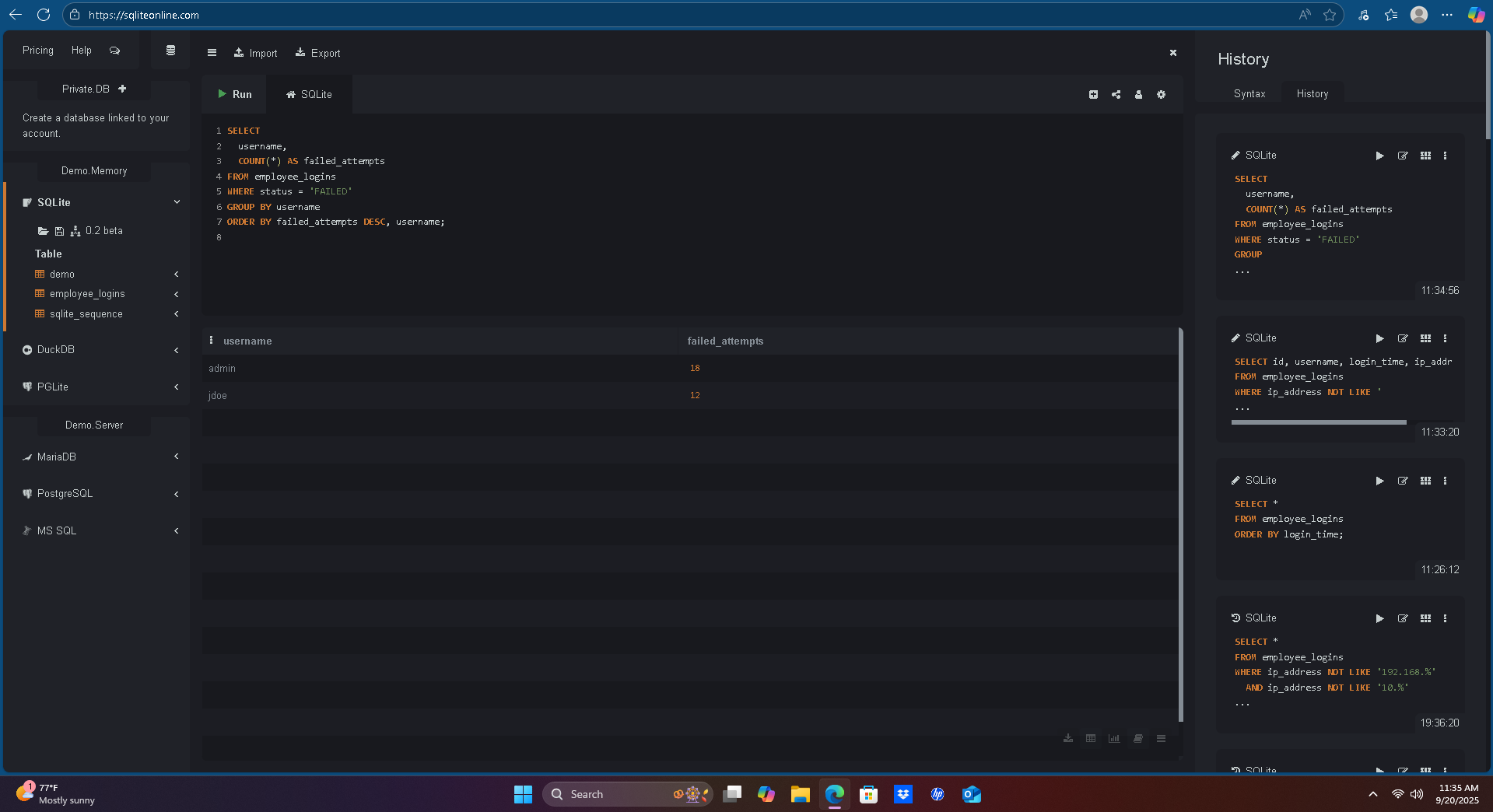
6) Failed Attempts per User
SELECT username, COUNT(*) AS failed_attempts
FROM employee_logins
WHERE status = 'FAILED'
GROUP BY username
ORDER BY failed_attempts DESC, username;
🚩 Findings
-
Multiple failed logins from
192.168.1.11and10.0.0.5. -
User
jdoeandadminshowed repeated failures before eventual success — common brute-force pattern. -
External logins from
203.0.113.55 (mary)indicate possible compromise from outside the network.
🧪 Labs & Practice (Google Cybersecurity Course)
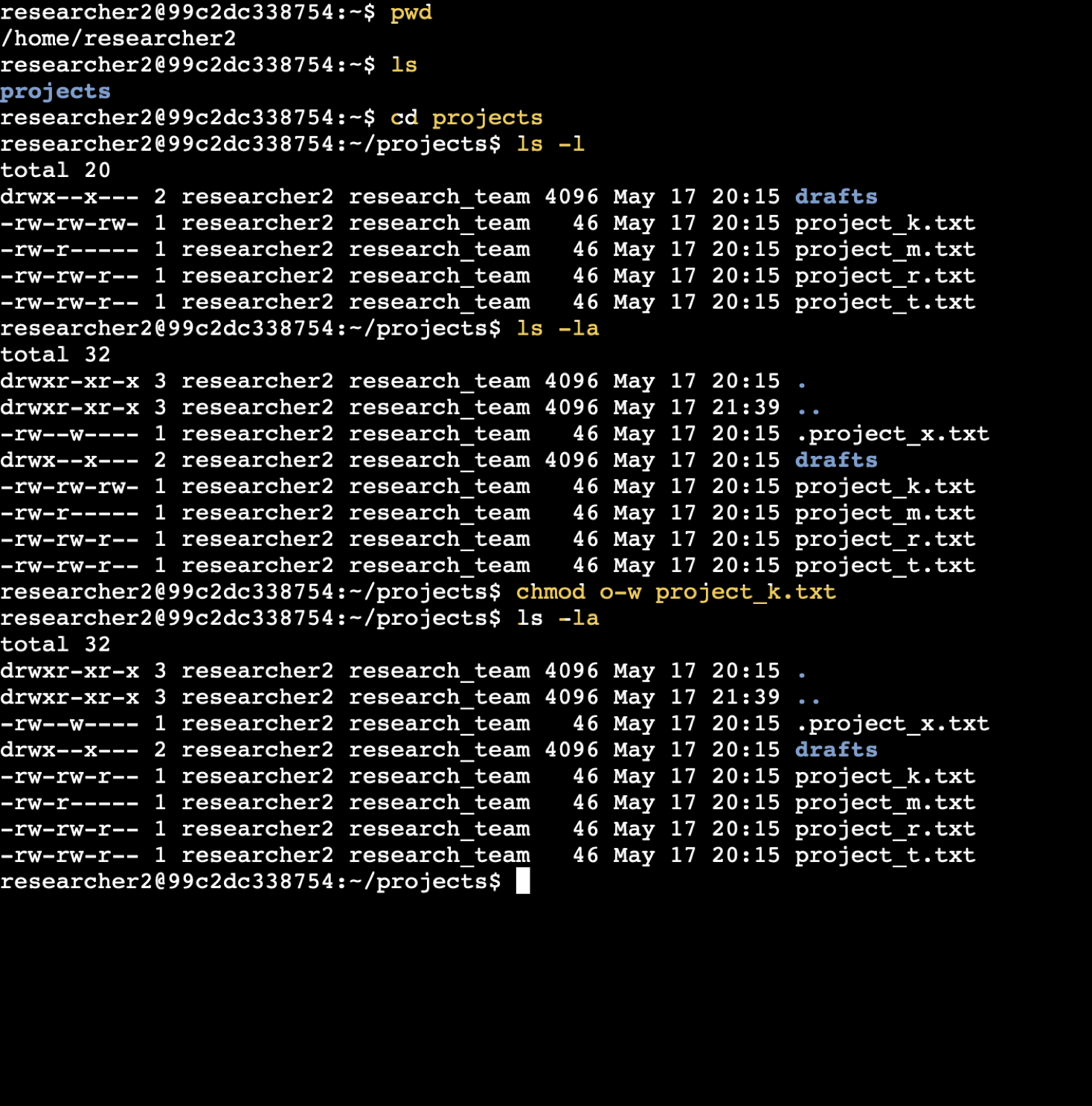
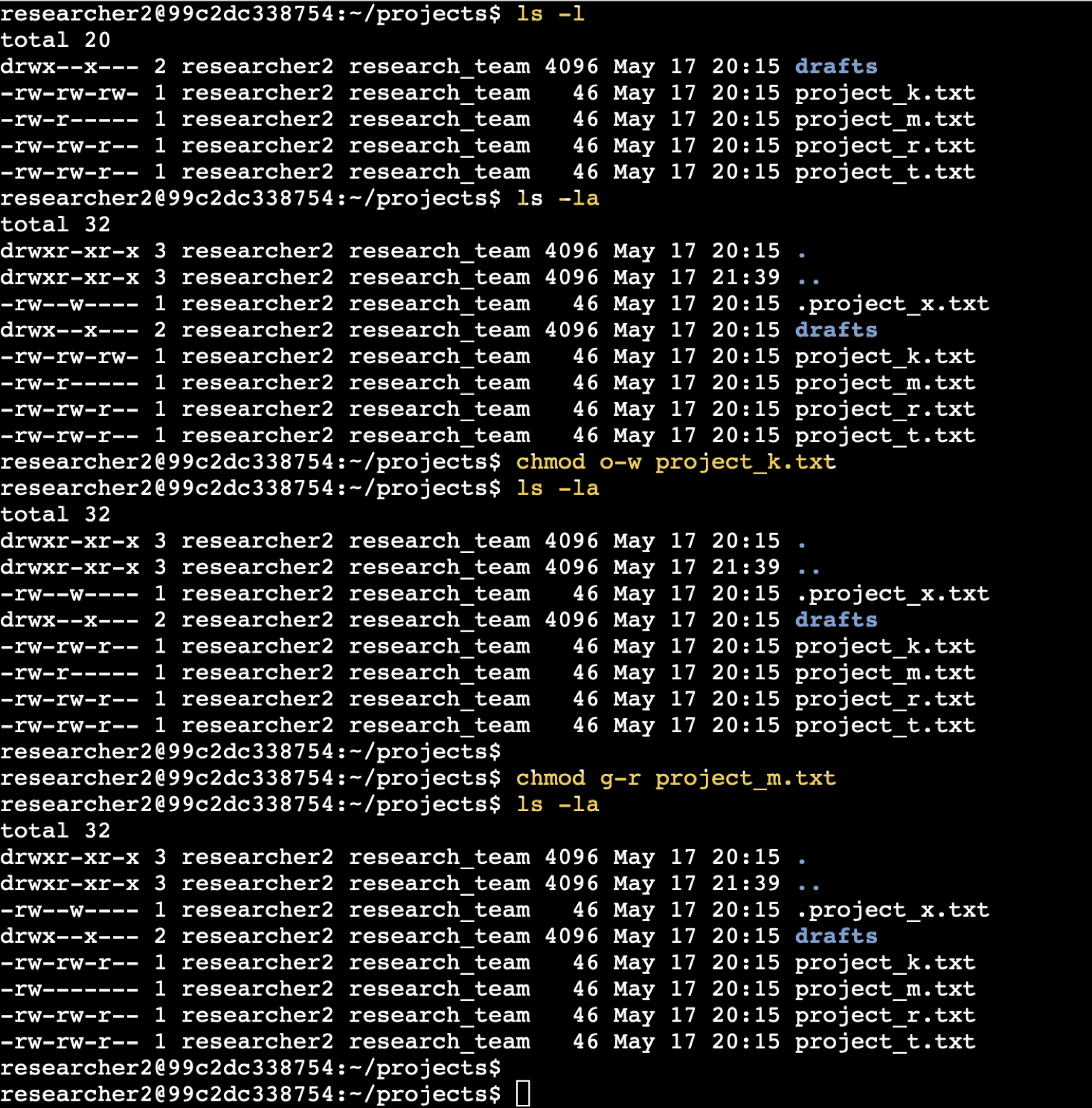
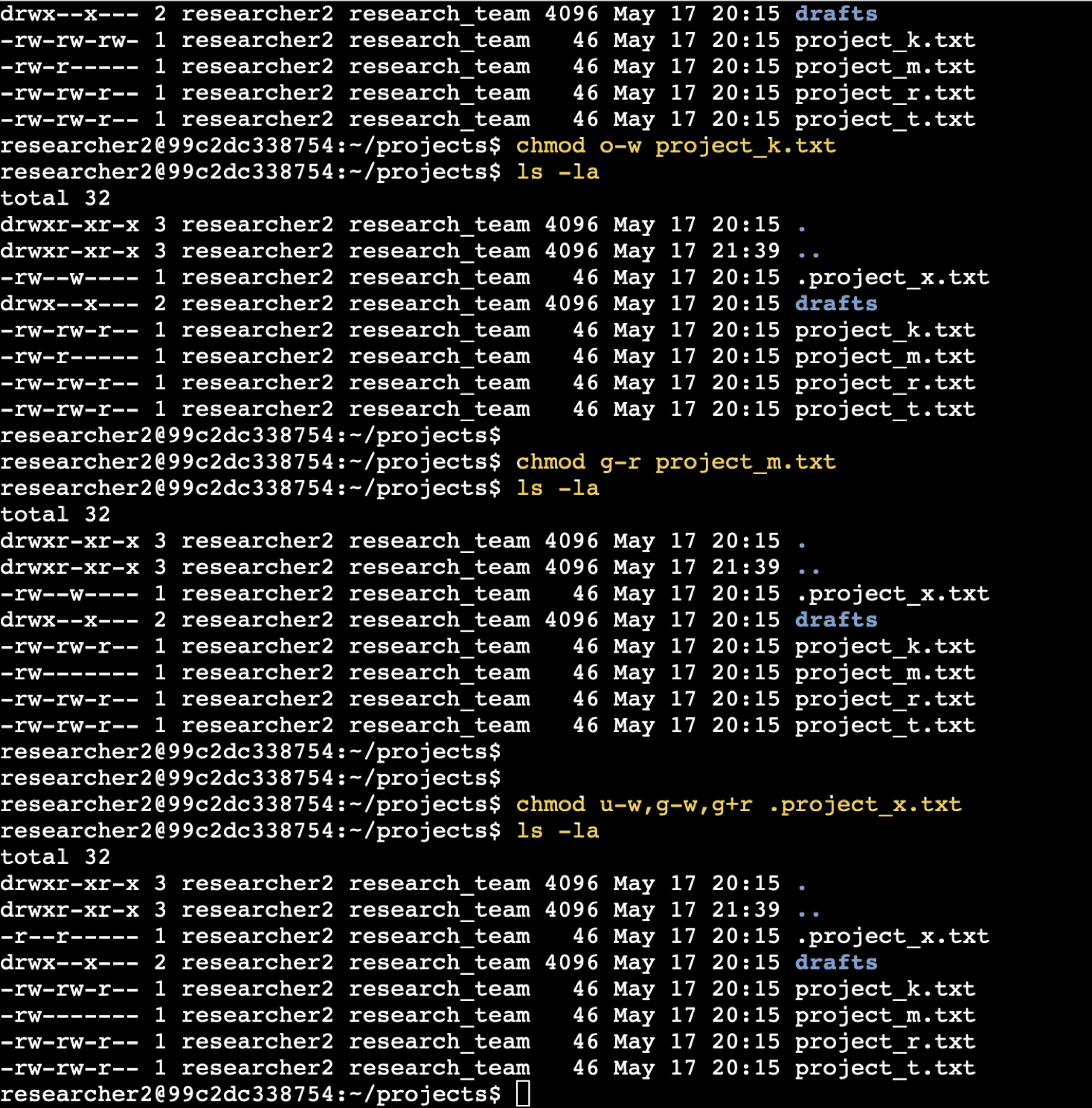
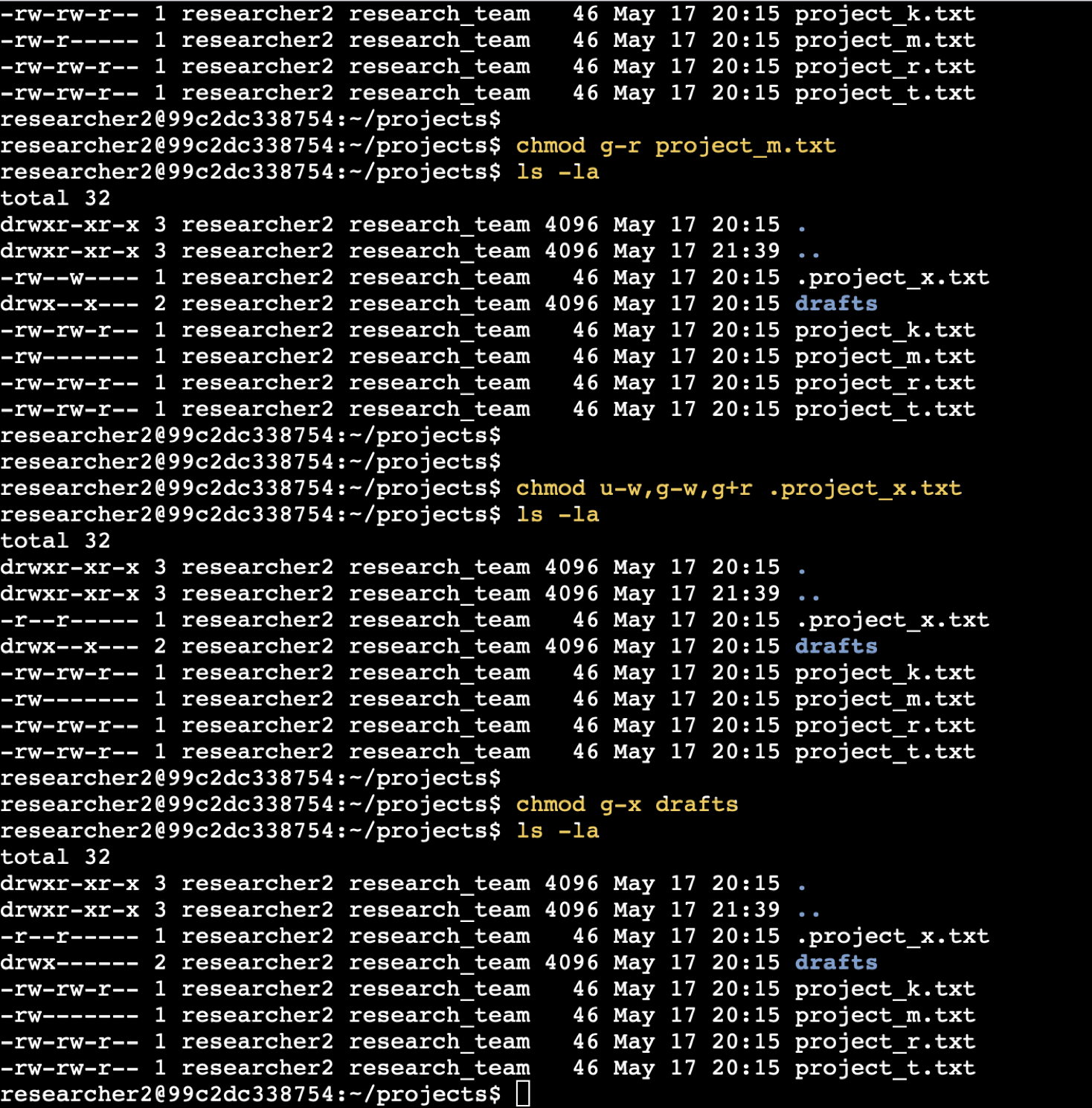
Manage Authorization (Linux Permissions)
🔒 Linux Permissions Lab – Click to Expand
PDFs
Screenshots
SQL Filtering – Data Investigation
📝 SQL Filtering – Detecting Failed Logins
PDFs
Screenshots
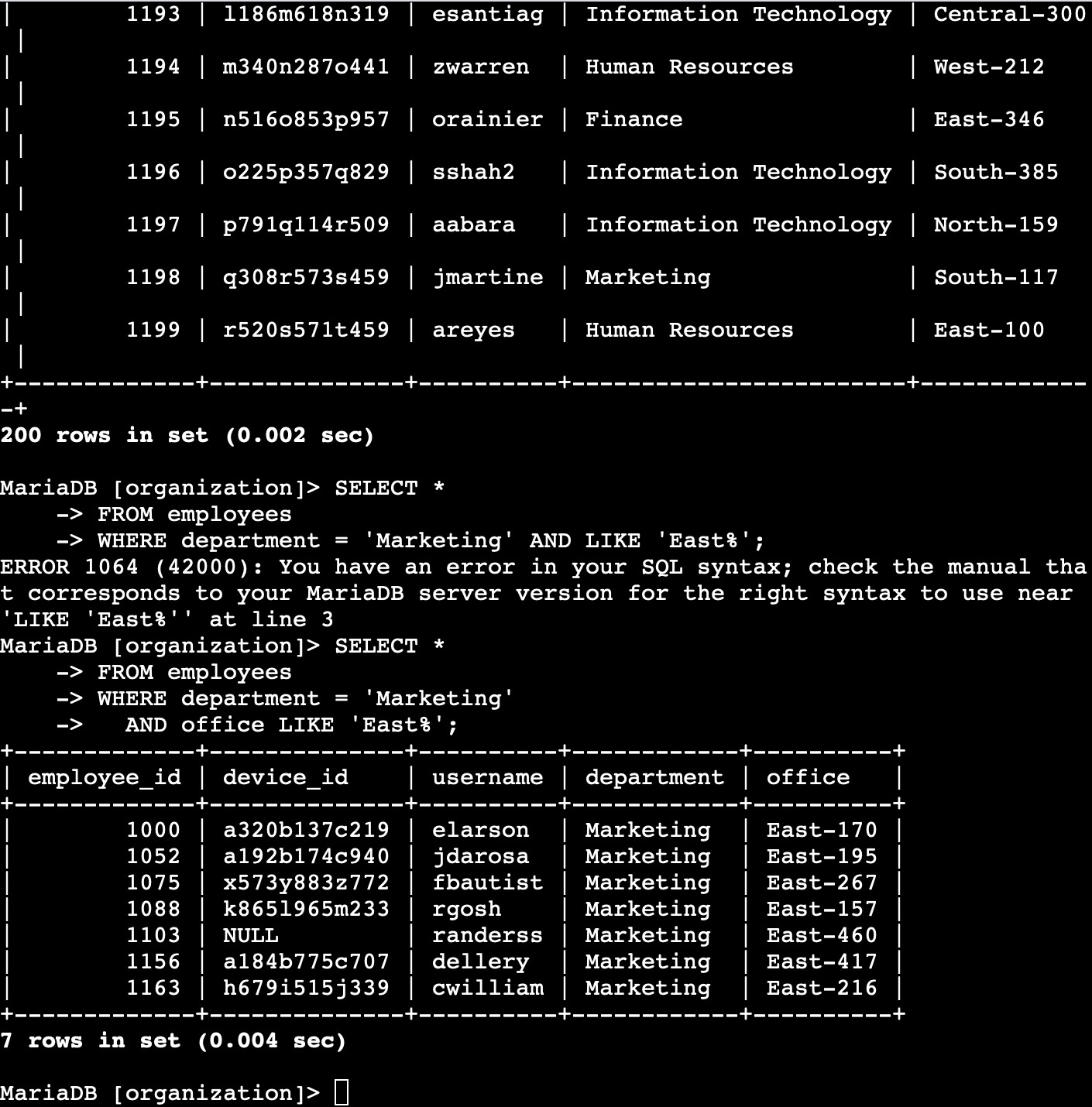
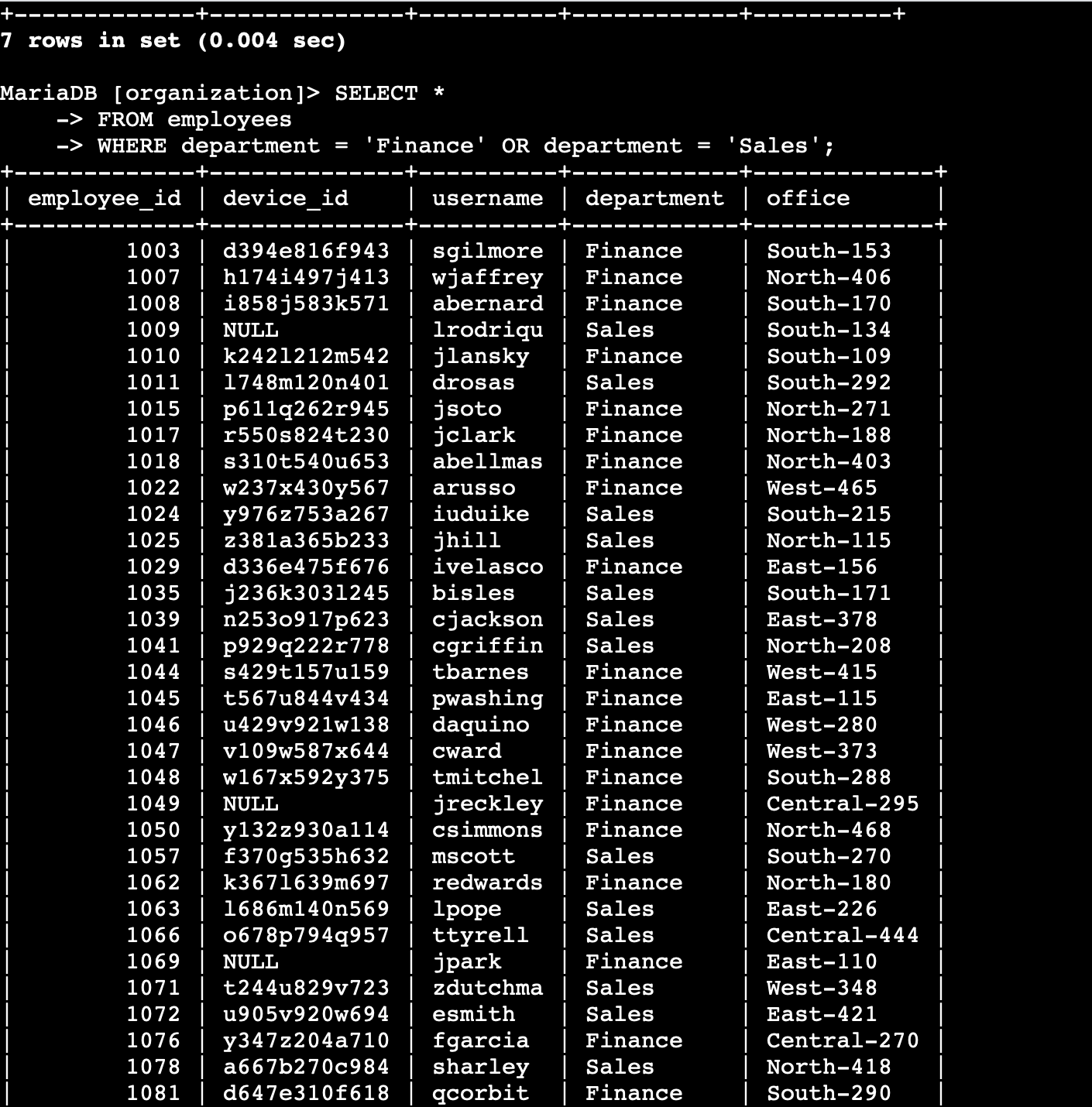
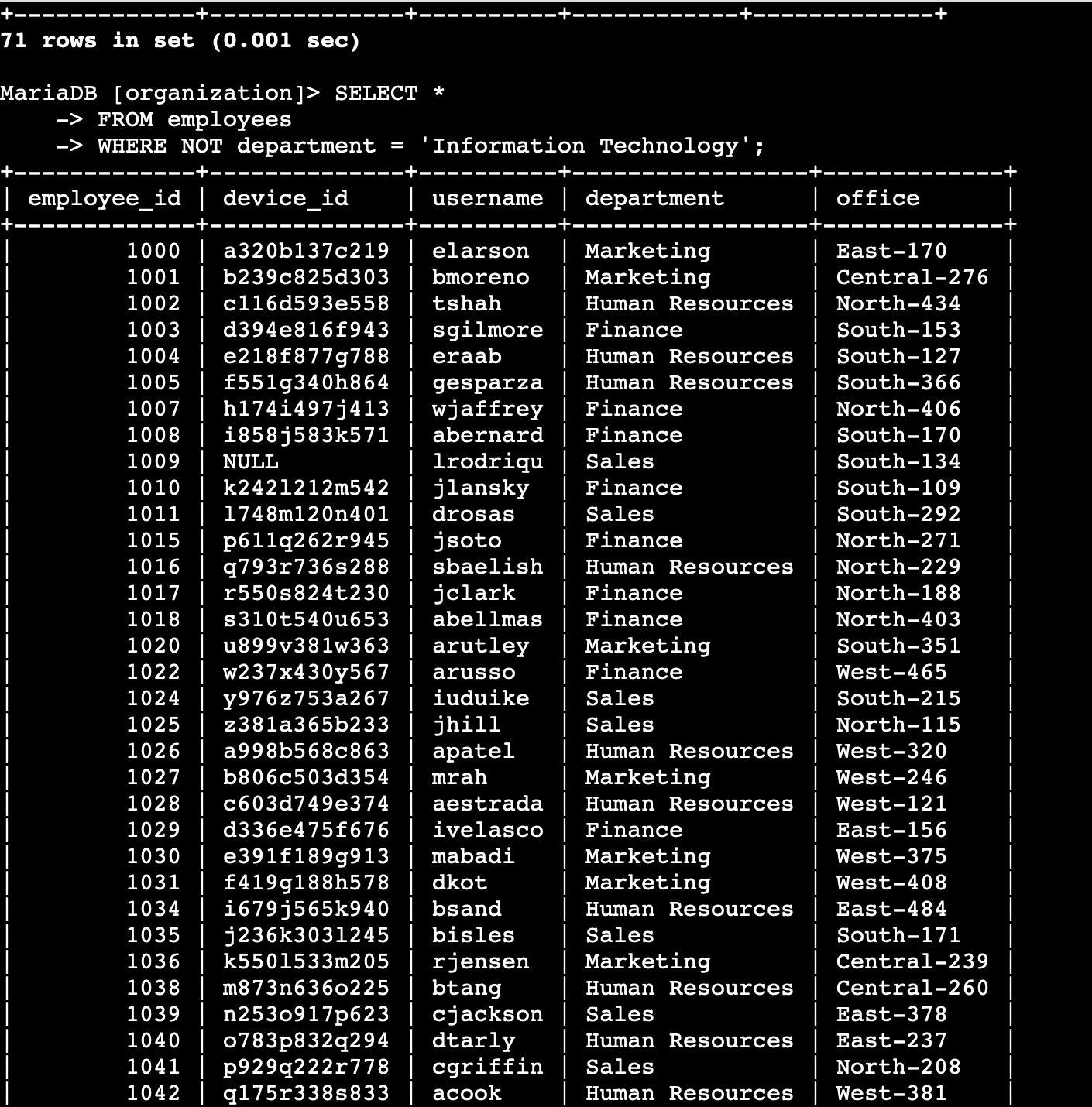
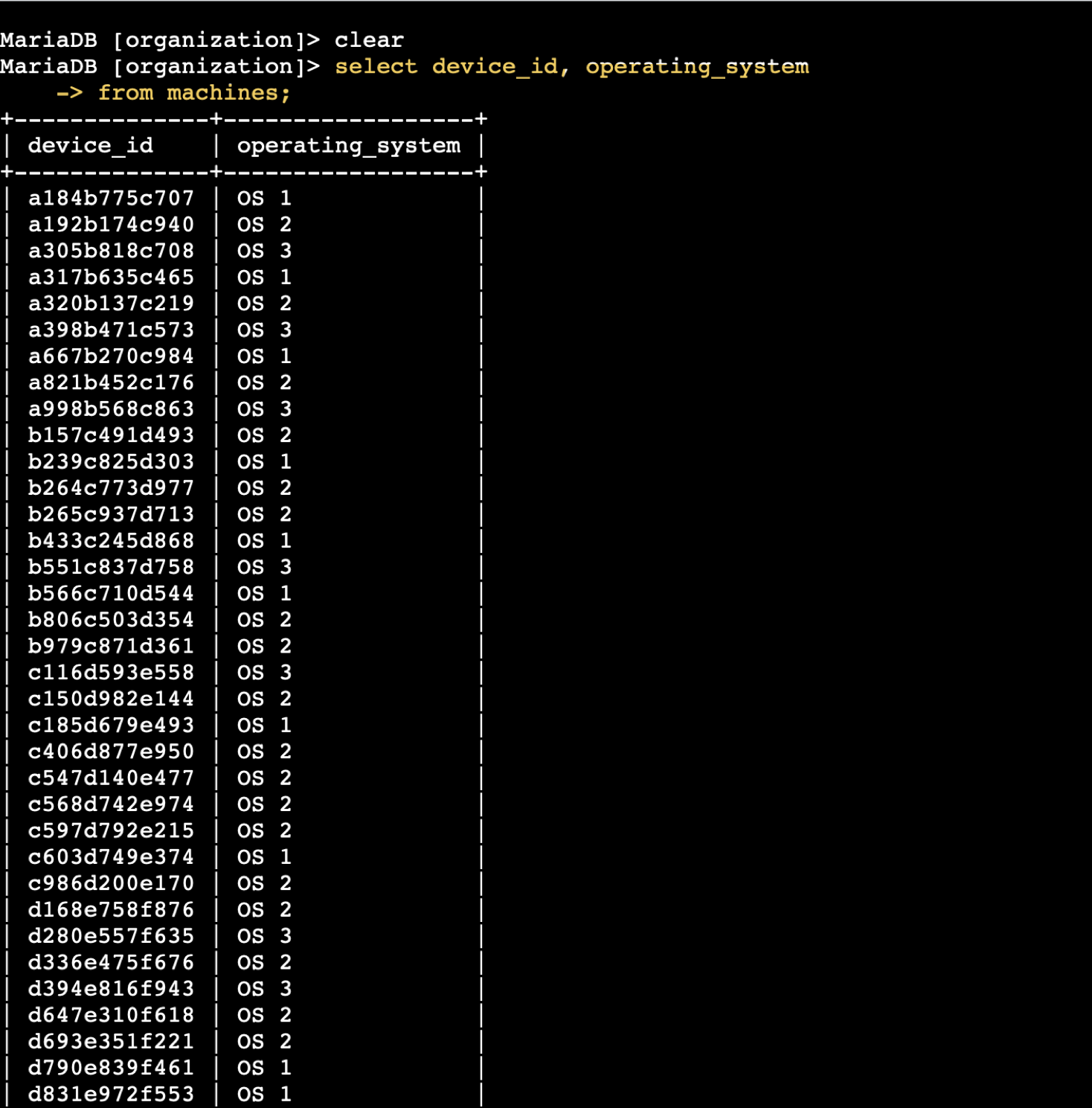
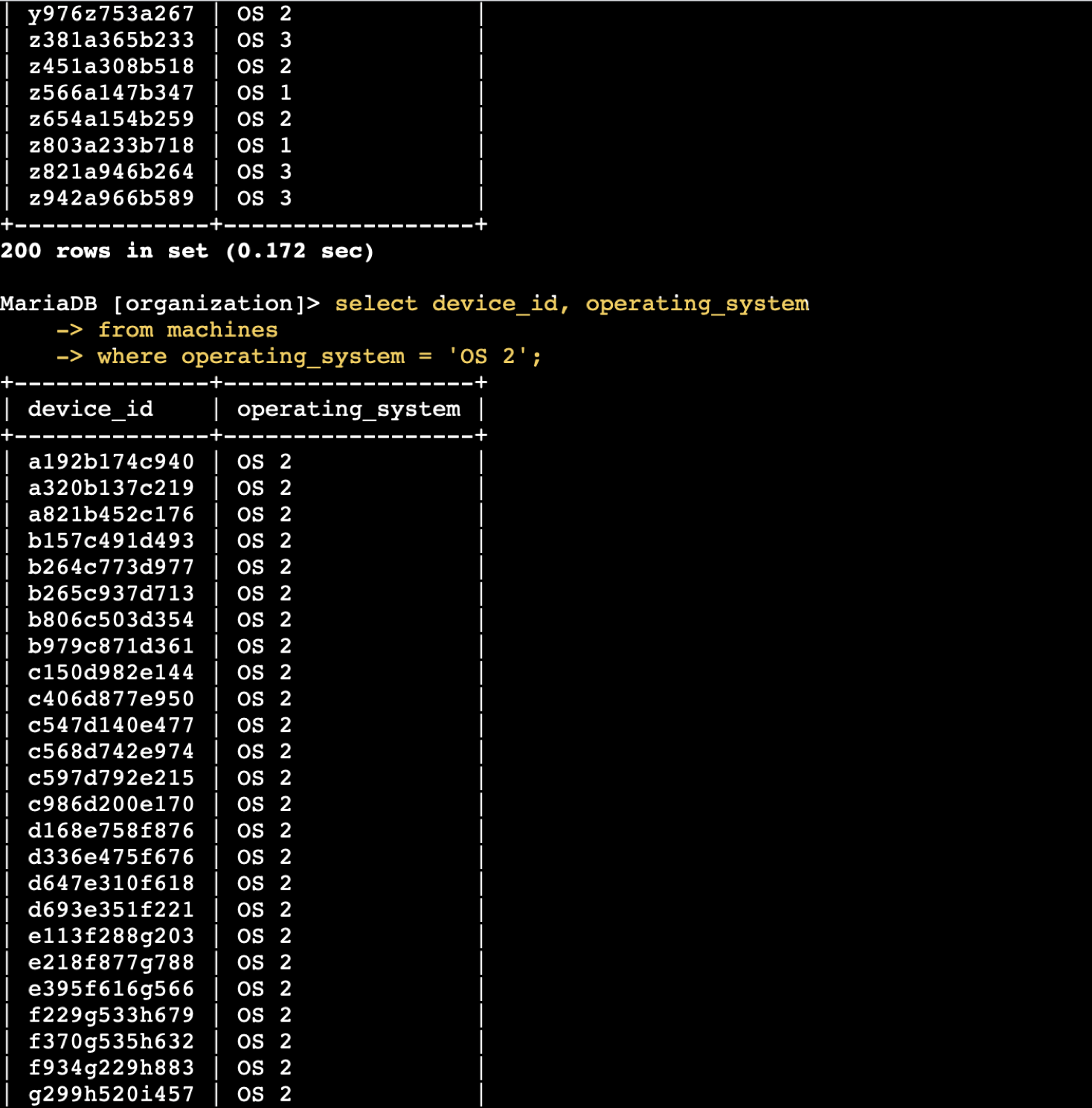
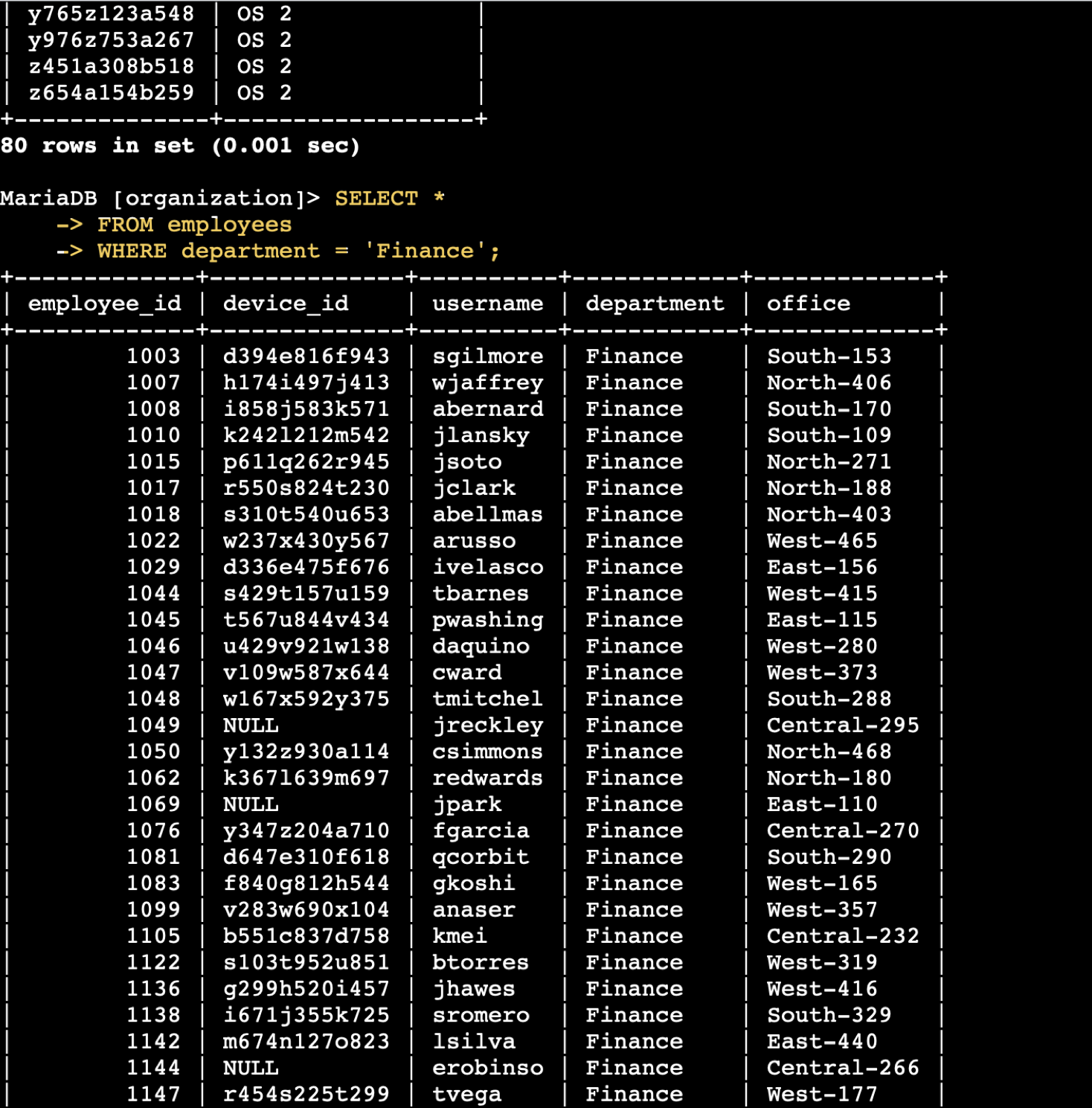
SQL Filtering – Employee & Machine Info
📌 Current Goals
-
Finish Google Cybersecurity Certificate
-
Build a home SOC lab (Kali Linux, Splunk, Security Onion)
-
Studying for comptia security+
-
Land an entry-level SOC role and keep leveling up
“I failed. I learned.” – That’s my mindset.